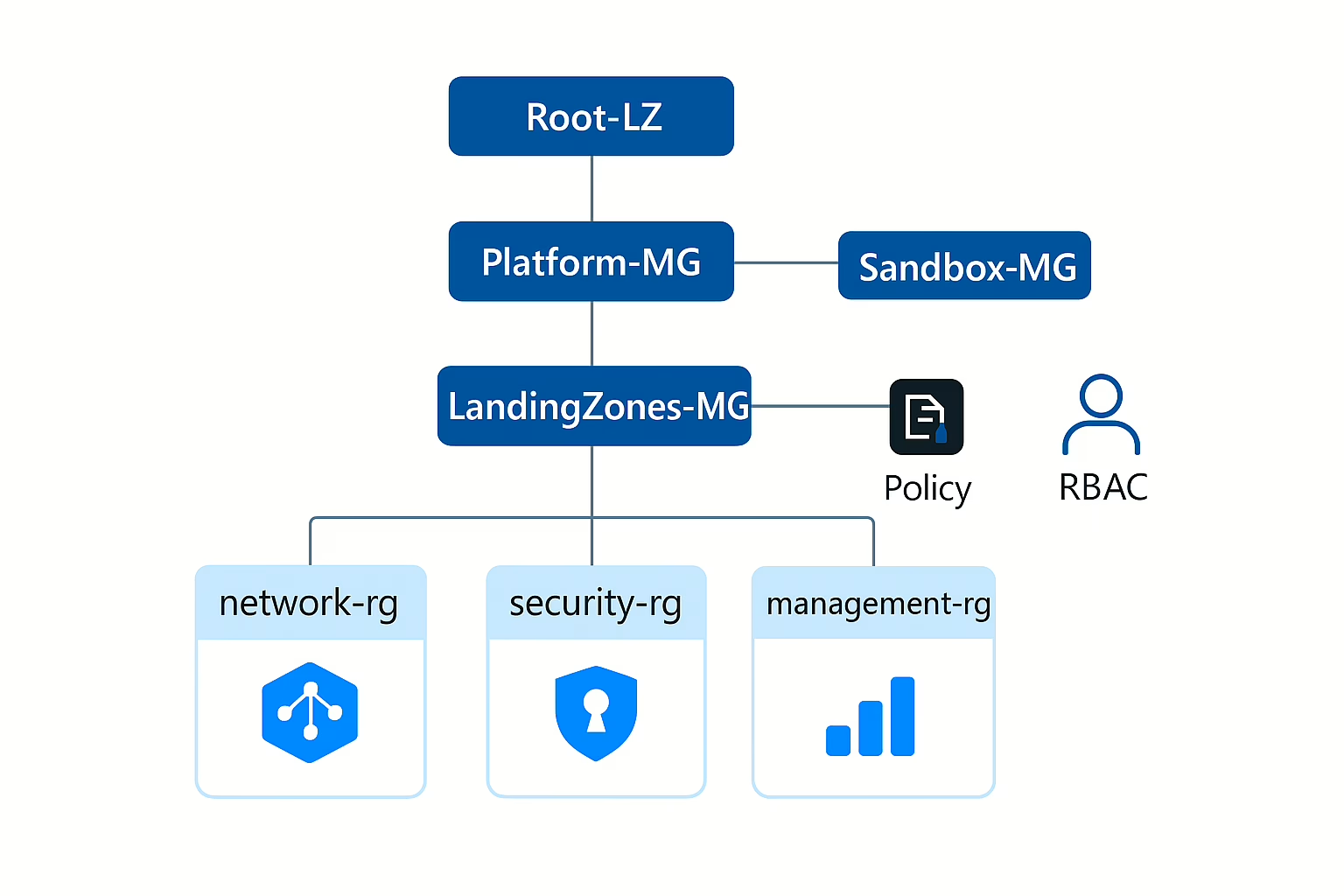
PoC Azure Landing Zone II – Management Group 포함 구성
PoC Azure Landing Zone 수준에서 Management Group 계층까지 포함된 Azure Landing Zone을 Terraform으로 구성하면, 엔터프라이즈 스케일의 기본 거버넌스 체계를 시연할 수 있습니다.
📌 PoC Azure Landing Zone – Management Group 포함 구성
- Management Group 계층 구조
Platform(공통 네트워크/보안/관리 리소스)LandingZones(업무 워크로드)Sandbox(개발/테스트용)
- Subscription 할당 (PoC에서는 실제 Subscription 연결 대신 구조만 정의 가능)
- Resource Groups + Network + Monitoring + Security (앞서 만든 리소스)
- Policy & RBAC 적용 (예: 태그 강제, 특정 사용자 Owner 권한)
✅ Terraform 예제: PoC Landing Zone with MG
terraform {
required_version = ">= 1.5.0"
required_providers {
azurerm = {
source = "hashicorp/azurerm"
version = "~> 3.100"
}
}
}
provider "azurerm" {
features {}
}
# ======================
# Variables
# ======================
variable "prefix" {
type = string
default = "poclz"
description = "Landing Zone prefix"
}
variable "location" {
type = string
default = "koreacentral"
description = "Azure region"
}
variable "owner_object_id" {
type = string
description = "RBAC 할당 대상 사용자/그룹의 AAD Object ID"
}
# ======================
# Management Group Hierarchy
# ======================
resource "azurerm_management_group" "platform" {
display_name = "Platform"
name = "${var.prefix}-platform"
}
resource "azurerm_management_group" "landingzones" {
display_name = "Landing Zones"
name = "${var.prefix}-landingzones"
}
resource "azurerm_management_group" "sandbox" {
display_name = "Sandbox"
name = "${var.prefix}-sandbox"
}
# Root 하위에 붙이기
resource "azurerm_management_group" "root" {
display_name = "Root-LZ"
name = "${var.prefix}-root"
}
resource "azurerm_management_group" "platform_child" {
display_name = "Platform-MG"
name = "${var.prefix}-platform-mg"
parent_management_group_id = azurerm_management_group.root.id
}
resource "azurerm_management_group" "landingzones_child" {
display_name = "LandingZones-MG"
name = "${var.prefix}-landingzones-mg"
parent_management_group_id = azurerm_management_group.root.id
}
resource "azurerm_management_group" "sandbox_child" {
display_name = "Sandbox-MG"
name = "${var.prefix}-sandbox-mg"
parent_management_group_id = azurerm_management_group.root.id
}
# ======================
# Resource Groups
# ======================
resource "azurerm_resource_group" "network_rg" {
name = "${var.prefix}-network-rg"
location = var.location
}
resource "azurerm_resource_group" "security_rg" {
name = "${var.prefix}-security-rg"
location = var.location
}
resource "azurerm_resource_group" "management_rg" {
name = "${var.prefix}-management-rg"
location = var.location
}
# ======================
# Networking (Hub VNET + Subnet)
# ======================
resource "azurerm_virtual_network" "hub_vnet" {
name = "${var.prefix}-hub-vnet"
location = var.location
resource_group_name = azurerm_resource_group.network_rg.name
address_space = ["10.10.0.0/16"]
}
resource "azurerm_subnet" "hub_subnet" {
name = "hub-subnet"
resource_group_name = azurerm_resource_group.network_rg.name
virtual_network_name = azurerm_virtual_network.hub_vnet.name
address_prefixes = ["10.10.1.0/24"]
}
# ======================
# Monitoring
# ======================
resource "azurerm_log_analytics_workspace" "log" {
name = "${var.prefix}-law"
location = var.location
resource_group_name = azurerm_resource_group.management_rg.name
sku = "PerGB2018"
retention_in_days = 30
}
# ======================
# Security Center
# ======================
resource "azurerm_security_center_contact" "security_contact" {
email = "security@example.com"
phone = "+821012345678"
alert_notifications = true
alerts_to_admins = true
}
# ======================
# Azure Policy (예: 리소스 그룹에 태그 강제)
# ======================
resource "azurerm_policy_definition" "tag_policy" {
name = "${var.prefix}-enforce-tag"
policy_type = "Custom"
mode = "All"
display_name = "Enforce 'Environment' tag on resource groups"
policy_rule = <<POLICY
{
"if": {
"field": "type",
"equals": "Microsoft.Resources/subscriptions/resourceGroups"
},
"then": {
"effect": "deny",
"details": {
"missingField": "tags['Environment']"
}
}
}
POLICY
}
resource "azurerm_policy_assignment" "tag_policy_assignment" {
name = "${var.prefix}-tag-policy-assignment"
display_name = "Enforce Environment Tag"
scope = azurerm_management_group.landingzones_child.id
policy_definition_id = azurerm_policy_definition.tag_policy.id
}
# ======================
# RBAC (예: Owner 역할 부여)
# ======================
resource "azurerm_role_assignment" "rg_owner" {
scope = azurerm_resource_group.network_rg.id
role_definition_name = "Owner"
principal_id = var.owner_object_id
}
📊 PoC 결과 구조

- Management Group 계층
- Root-LZ
├── Platform-MG
├── LandingZones-MG
└── Sandbox-MG
- Root-LZ
- Resource Groups
poclz-network-rgpoclz-security-rgpoclz-management-rg
- Networking
- Hub VNET (
10.10.0.0/16) - Subnet (
10.10.1.0/24)
- Hub VNET (
- Governance
- Policy: LandingZones-MG 아래 모든 RG에
Environment태그 강제 - RBAC: 특정 Object ID에
Owner권한 부여
- Policy: LandingZones-MG 아래 모든 RG에